The vulnerability let attackers remotely gain control of some devices running Intel AMT, potentially executing code or stealing data. Estimates put the number of affected servers at 7,000, but the millions of PCs that connect to those could also be at risk. Thankfully, Microsoft Surface devices aren’t one of them. In a blog post on Thursday, Redmond contractor Brandon Records reassured users: “In the beginning of May, Intel announced that a vulnerability had been detected in their Intel® Active Management Technology (AMT), available in many of their processors and chipsets including some processors and chipsets used in the Surface device lineup,” the lead of Microsoft’s outreach team explained. “Devices in the Surface lineup are not vulnerable to this exploit and no action is required on the part of administrators or users.”
The Intel SA-00075 Discovery Tool
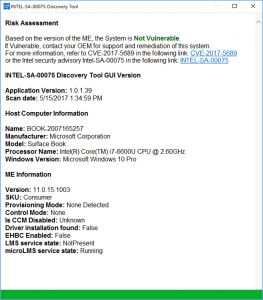
To prove this, Records shared a screenshot of Intel’s Discovery Tool. It shows that an i7 Surface Book running Windows 10 Pro is not vulnerable to the Intel AMT exploit.
However, if you want to test a different device, its easy to run the Discovery Tool yourself. You simply download and install it from the Intel Download Center, following the simple guide. Hopefully, this should both allay fears for Surface users and stop admins implementing solutions unnecessarily. If you’re still worried, you can read more about the specifics on the Intel Advisory.